Hardening the MFT Server Environment
This section provides a list of things you can do to harden your MFT server environment. In order to provide you with optimal protection, many security features need to be activated or in some cases disabled.
Not all file transfer servers need to be configured to a high level of security. Some security functions, like strong encryption, are computationally expensive and can cause performance issues. If you are not exchanging any sensitive data and your servers are not high-performance grade, you likely don't need to enable every single security feature available. Alternatively, some organization operate in a highly regulated industry, and they need to comply with data protection laws and regulations like HIPAA and PCI DSS. When this is the case, they will likely need to harden their MFT server environment to avoid penalties.
1) Disable plain FTP
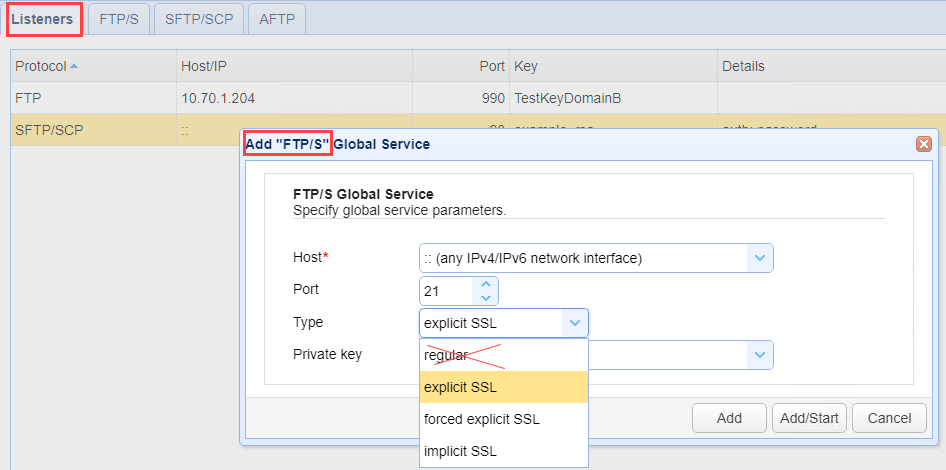
Plain (i.e. regular) FTP is not secure. While MFT Server does allow for its usage, it is recommended that secure file transfer protocols like SFTP, FTPS, and HTTPS are used instead.
When you are adding global or domain-level services, avoid selecting regular FTP. Services are managed in the domain-level SERVICES > Listeners module and the Settings > GLOBAL SERVICES > Listeners modules.
2) Enable password compliance policies
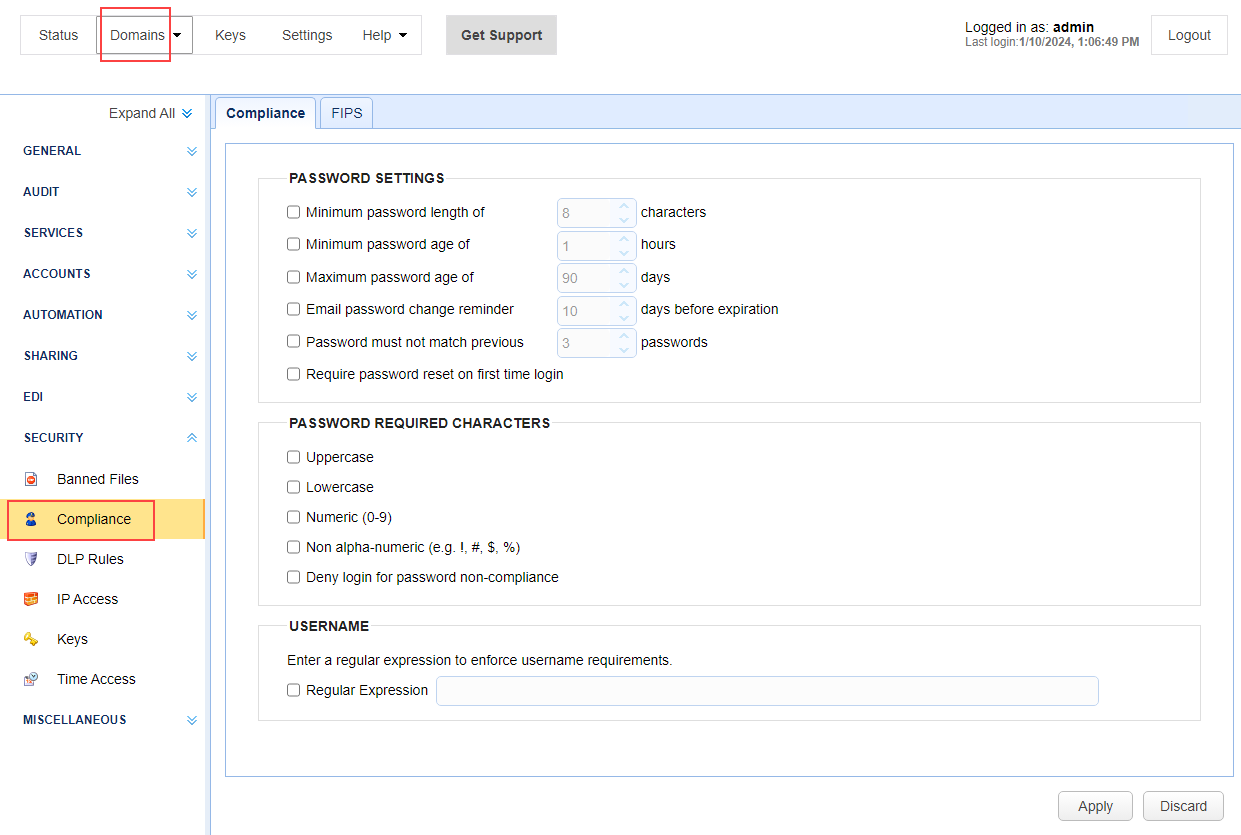
Weak passwords are more vulnerable to dictionary or brute force attacks. The best way to counter these attacks is by implementing a strong password policy. You are likely familiar with hearing something like this: Use passwords that consist of uppercase and lowercase letters, numbers, and non-alphanumeric characters, and having a minimum length of 10 characters.
To make sure your password policy is enforced, you need to configure server settings on the domain-level. See the SECURITY > Compliance module. Once activated, users will have to abide by your password policies.
See also: Compliance settings
3) Detect and respond to brute force attacks
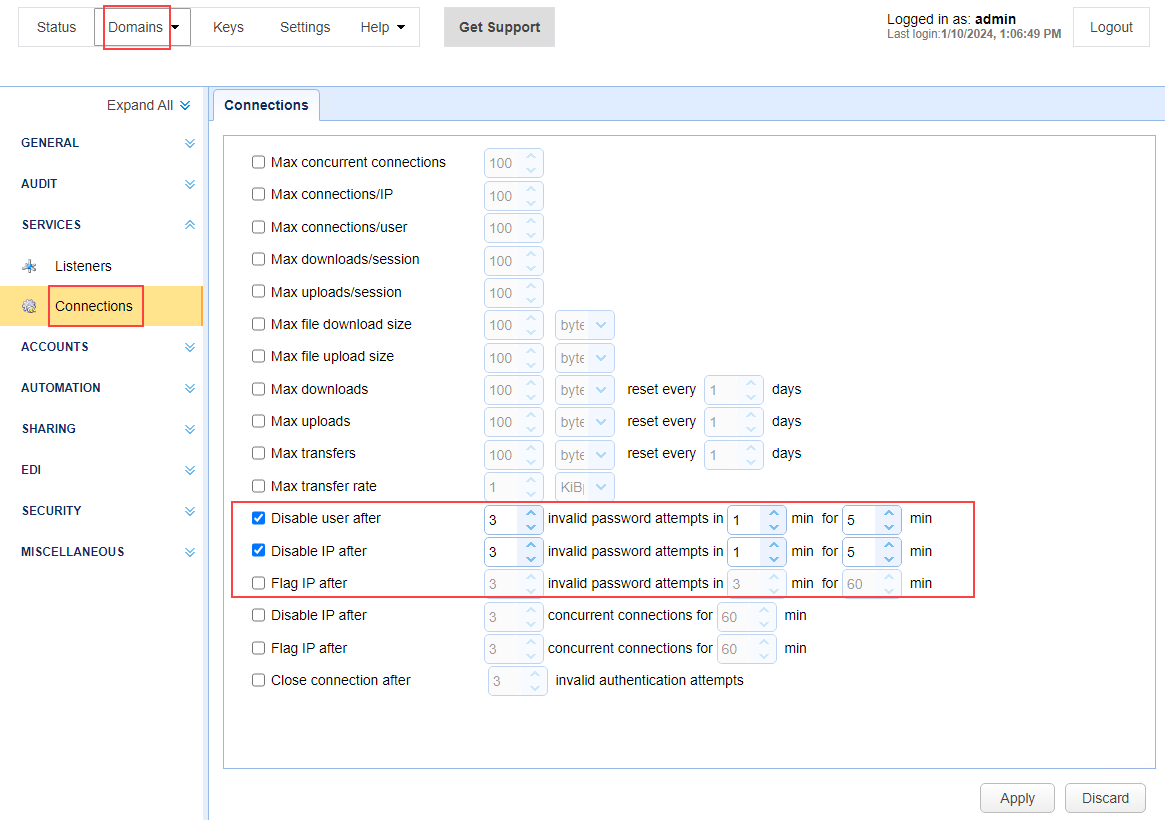
Brute force attacks use hacking tools to try and guess passwords to gain access to your MFT server. Attacks can cause FTP log files to fill up with failed access attempts, and adversely impact the MFT server's performance. There are domain-level connection settings you can configure to handle this type of event, should it occur. See the domain-level SERVICES > Connections module. In looking at the image below, an account can automatically be disabled, or an IP address can be blocked (or flagged) after a specified number of login attempts has occurred.
See also: Setting connection preferences
4) Disable weak encryption ciphers
Secure file transfer protocols like FTPS, SFTP, and HTTPS are equipped with encryption capabilities to preserve the confidentiality of data during transmission. However, some ciphers are stronger than others. Therefore, if you are frequently transmitting highly sensitive information, you should not be using weak ciphers.
To use strong ciphers on MFT Server, make sure you use the latest version of Java and install the JCE Unlimited Strength Jurisdiction Policy Files.
Next, configure the FTPS, SFTP, and HTTPS protocols using only strong ciphers.
For FTPS, you can configure strong ciphers for domain and global services.
For domain services, navigate to the desired domain, then select the
SERVICES > Listeners > FTP/S >tab and click on the SSL/TLS ciphers button.For global services, navigate to the
Settings > GLOBAL SERVICES > Listeners > FTP/Stab and click on the SSL/TLS ciphers button.
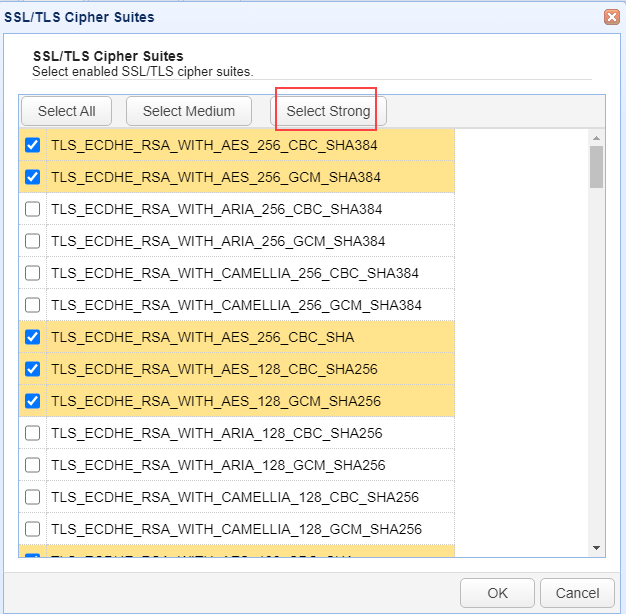
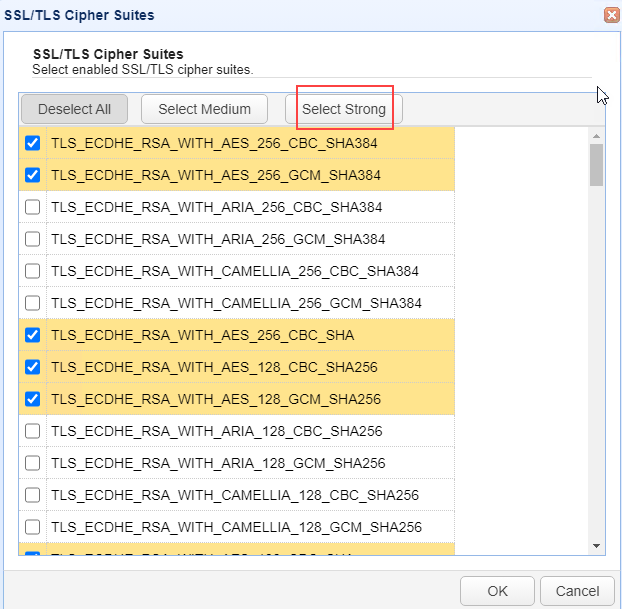
In both cases, you will see a page as depicted in the image below. Click on the Select Strong button.
For SFTP, you can configure algorithms for domain and global services.
For domain services, navigate to the desired domain, then select the
SERVICES > Listeners > SFTP/SCPtab and click on the Algorithms button.For global services, navigate to the
Settings > GLOBAL SERVICES > Listeners > SFTP/SCPtab and click on the Algorithms button.
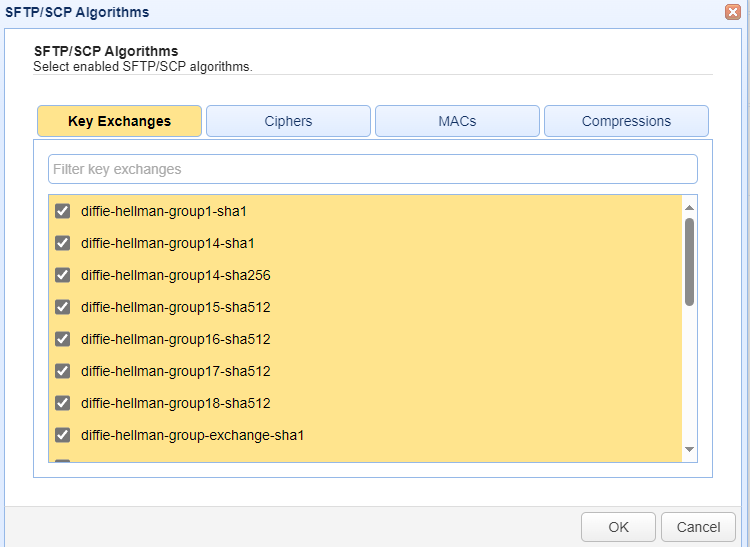
In both cases, you will see a page as depicted in the image below. Select the Key Exchange, Cipher, MAC, and Compressions that meet your security requirements. You can optionally use the filter feature to pare down the list. If used, only items that have matching characters will remain visible in the list.
For HTTPS, you can configure ciphers by navigating to Settings > MISCELLANEOUS > Web > Web. Under the HTTPS heading, click on the SSL/TLS Ciphers button.
You will see a page as depicted in the image below. Click on the Select Strong button.
If you need to adhere to very strict security policies but are not sure which ciphers to enable/disable, then the easiest way would be to simply enable FIPS compliance. You can apply FIPS compliance to HTTPS, FTP/S, and SFTP.
5) Scan incoming files for viruses
Due to the sheer volume of files that are uploaded to file transfer servers, there is always the concern that files may be infected with malware. Some types of malware, like ransomware, can cripple entire networks or, in the case of WannaCry, multiple networks.
It is important to employ solutions that detect and eliminate these threats as they enter your server. MFT Server supports various methods of integrating with virus solutions to address these threats. MFT Server can work with an antivirus software that's installed locally on the same machine or connect to an ICAP antivirus server and offload the scanning to it.
6) Inspect outgoing content using DLP (Data Loss Prevention)
Some data breaches happen as a result of a deliberate cyber attack. Others happen unintentionally, like a user accidentally uploading a spreadsheet containing highly confidential data to a shared folder.
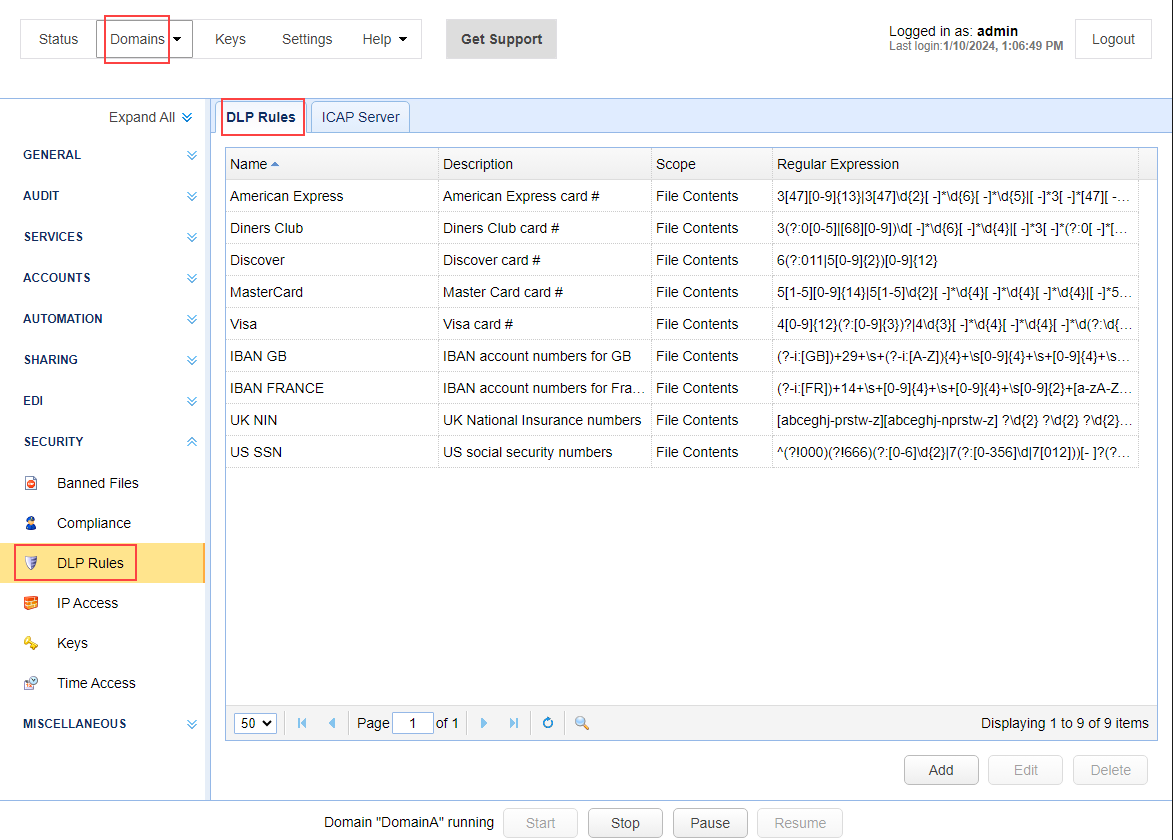
To prevent accidental data leaks, implement the DLP (data loss prevention) feature. The built-in DLP rules of MFT Server can already detect several types of sensitive data, including: credit card numbers, IBAN account numbers, UK National Insurance Numbers, and US Social Security Numbers. Additionally, you can add more rules by navigating to the desired domain, then selecting SECURITY > DLP Rules > DLP Rules.
See also:
Using DLP to Protect Credit Card Data
7) Encrypt data at rest
In the prior sections we highlighted the importance of using encrypted file transfer protocols like FTPS, SFTP, and HTTPS. These protocols encrypt data while in transit. But, it is equally important to encrypt data while at rest (i.e. while it is being stored). Should your storage device get compromised, the contents of the files stored there will still be able to preserve their confidentiality.
Data at rest encryption is provided using MFT server's OpenPGP functionality. The way you would leverage OpenPGP encryption is through any of the following methods:
See also OpenPGP Keys
8) Enforce IP Access rules
One way to mitigate unauthorized access to your MFT server is by enforcing IP access rules. An IP access rule restricts access to your server (through blacklisting or whitelisting) from machines/devices with specific IP addresses or IP addresses within a specified range. This would limit the amount of inbound connections and also make it more difficult for an attacker to login to your server - even if he/she managed to steal a valid account's login credentials. If the attacker attempts to connect from a non-whitelisted IP address, the connection request would be denied.
IP access rules can be applied to the following areas:
-
In
Settings > MANAGER SERVICE > Manager Service. Click on the Access tab (this is for server admins). -
In the desired domain's
SECURITY > IPmodule. Click on the Access tab (this is for domain-wide IP access restrictions). -
In the desired domain's
ACCOUNTS > Usersmodue. When adding or editing a user, click on the IP Access tab.
See also:
9) Enable Multi-Factor Authentication
Multi-factor authentication is a combination of two or more factors of authentication. For example, you can combine password and public key authentication, or password and the user's mobile phone (e.g. TOTP), and so on.
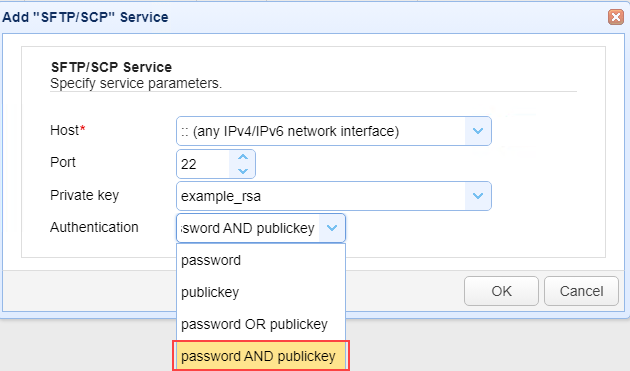
Below is an example of configuring an SFTP service where authentication is configured to use a password AND public key.
As another example, enabling multi-factor authentication requires you select the desired domain, then navigate to ACCOUNTS > Authentication, then click on the Multi-Factor Authentication tab. Select the type from the dropdown list.
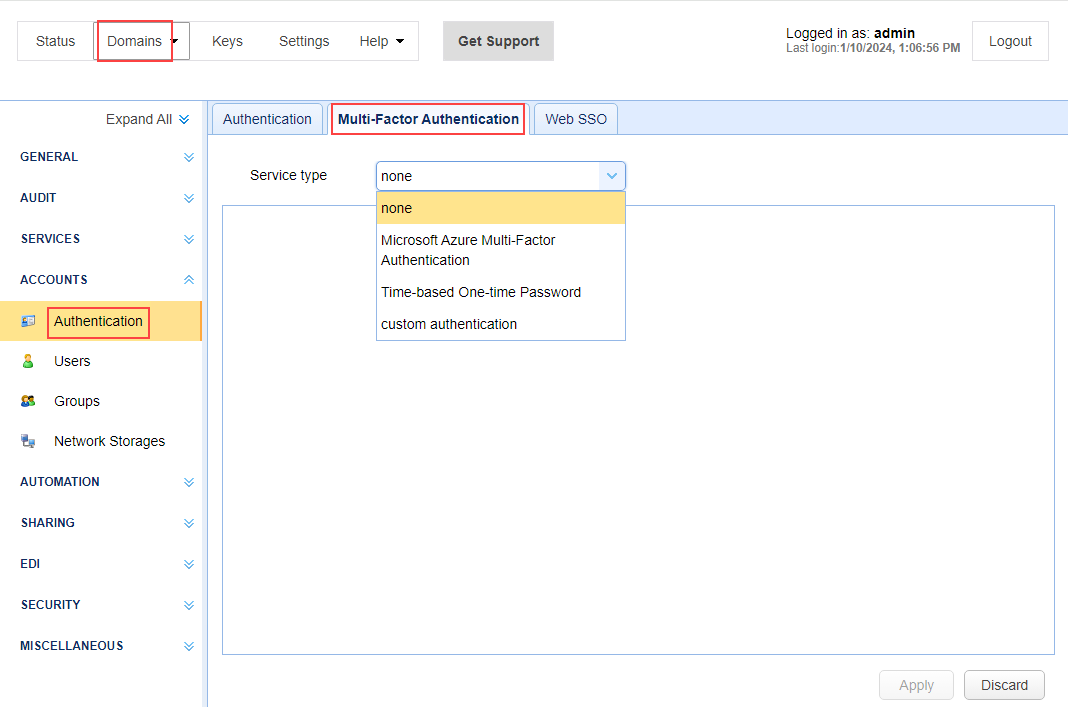
See also: Using Multi-Factor Authentication
10) Restrict file types
If you only expect certain file types to be uploaded to your server, you can create a whitelist to ban all other types. This will prevent you from encountering issues like:
-
Malware infections (some files are actually trojans disguised as pdf or docx files)
-
Unnecessary uploads that only consume disk space
-
Legal issues caused by uploading of pirated media
To access this feature, select the desired domain, then navigate to SECURITY > Banned Files.
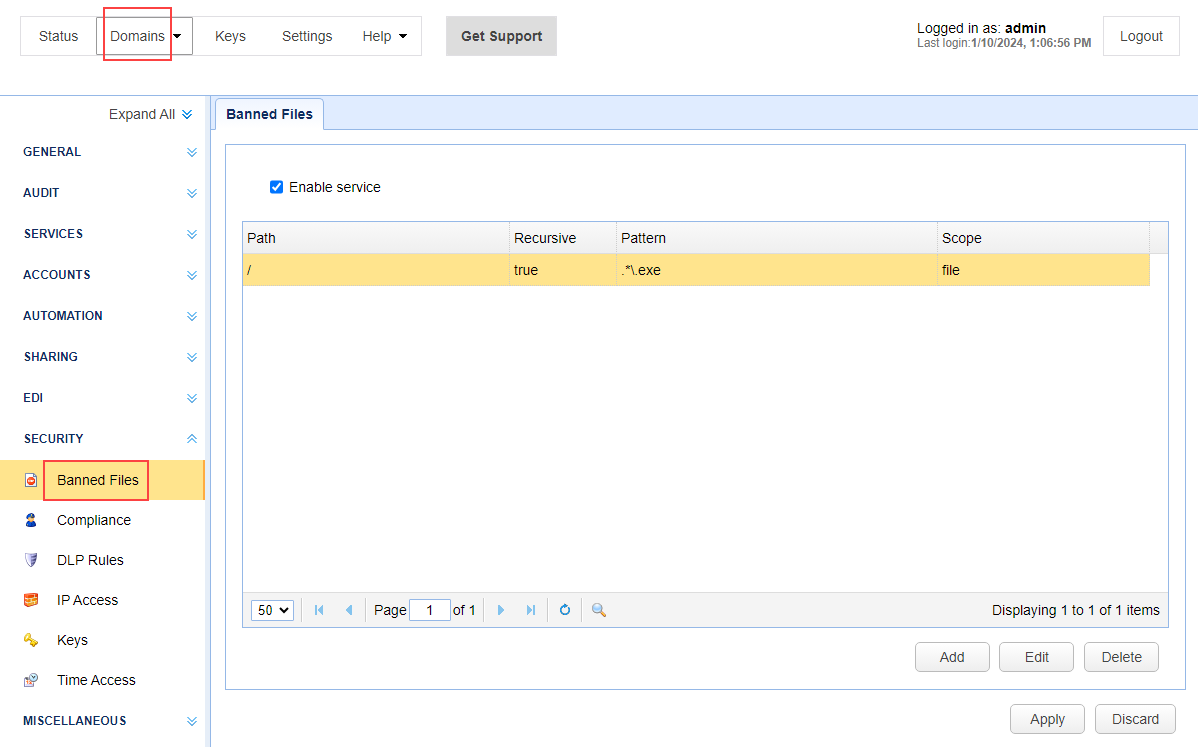
See also: Setting banned files
11) Restrict Time Access
You can restrict the time clients can access your server. Some reasons for implementing this include:
-
You have limited network bandwidth and want to prevent file transfers from interfering with other business operations during certain hours
-
You want to closely monitor transfers and don't want them taking place outside office hours
-
You want to minimize the chances of non-work related transmissions
To configure this, select the desired domain, then navigate to SECURITY > Time Access
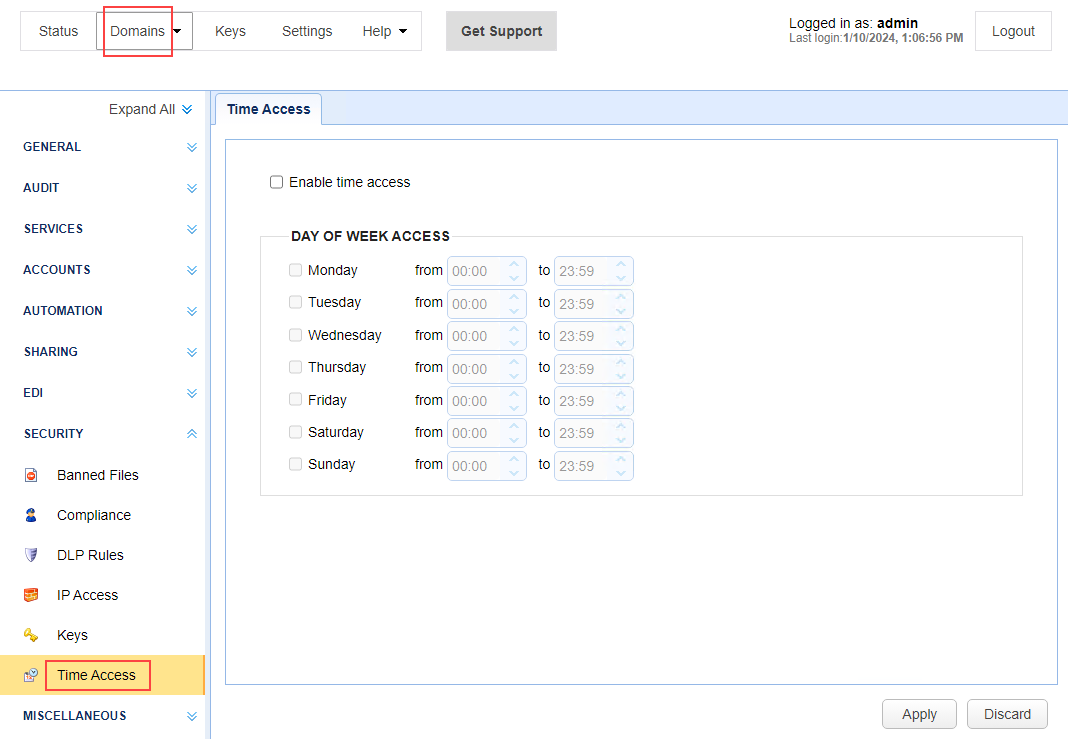
See also: Setting time based access
12) Manage and monitor your logs
Log files can be used for troubleshooting purposes and for digital forensics if something goes wrong (e.g. your server is hacked).
-
Server logs are stored in the [mft server installdir]/var/log directory.
-
File-based domain logs can be found in the directory specified in
AUDIT > Logging > Service > Directory. -
Database domain logs can be found in the database specified in
AUDIT > Logging > Service > JDBC URL.
You also have the option to store domain log entries in a Syslog service or a Splunk deployment.
If you are conducting an investigation and want to find certain entries/events in your domain logs, you can implement a search in the Search tab. See AUDIT > Logging > Search.
13) Stay up-to-date
Software patches and upgrades include new features and enhancements that improve performance and efficiency. They can also include vulnerability fixes as well as new security features and enhancements. New versions are typically released four times a year, and patches are made available as necessary.
See also: Updates