Compliance settings
The Compliance module provides various settings designed to meet regulatory compliance requirements, particularly those pertaining to PASSWORD SETTINGS, USERNAME, and FIPS.
To configure password requirements, navigate to the SECURITY > Compliance module. The Compliance tab is active by default.
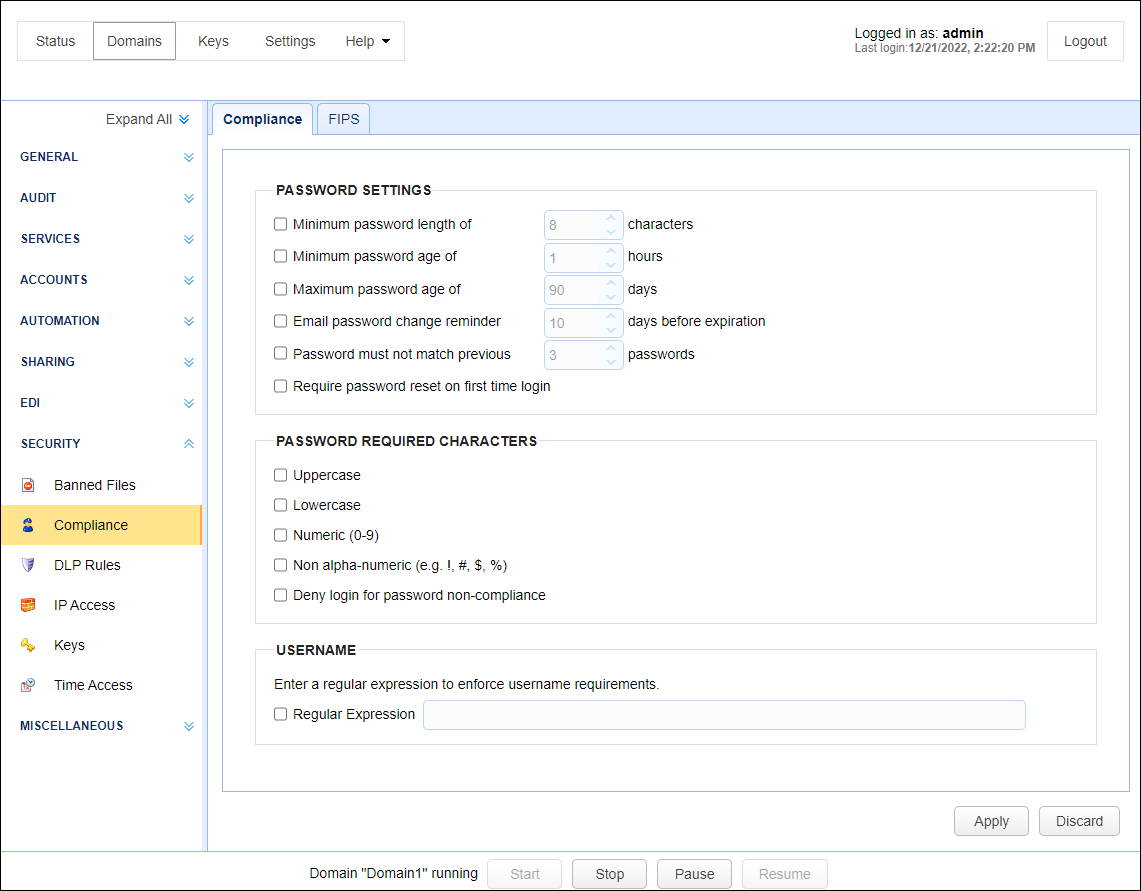
Below is a description of the compliance fields. Select any setting you wish to enable, and if required, specify a value.
Minimum password length of X characters — Identifies the minimum password length.
Minimum password age of X hours — Identifies the minimum number of hours that must go by before a password can be changed. Administrators can change passwords regardless of this setting.
Maximum password age of X days — Identifies the maximum number of days that a password is valid before it must be changed. This option can be overridden at the User-level by enabling the Ignore password aging rules option.
Email password change reminder X days before expiration — Emails a password change reminder to the email address associated with User the specified number of days before the password reaches its maximum password age. To work as expected, an SMTP server must be configured under Settings > MISCELLANEOUS > Email in the MFT Server Manager.
Password must not match previous X passwords — Identifies the number of previous passwords that cannot match the new password.
Require password reset on first time log in — Requires a new User resets their password the first time they log in.
PASSWORD REQUIRED CHARACTERS
Uppercase — If selected, an uppercase character must be included in the password.
Lowercase — If selected, a lowercase character must be included in the password.
Numeric — If selected, a numeric value (0-9) must be included in the password.
Non alpha-numeric — If selected, a special character (e.g., %, #, !) must be included in the password.
Deny login for password non-compliance — If enabled, the password is verified at the time of log in, to check that it meets compliance requirements. If it matches the User password, but does not meet compliance requirements, access is denied.
Enter a regular expression to enforce user name requirements
Regular Expression — If selected, enter a regular expression that specifies the pattern that must be used when a new User is created.
The FIPS tab displays a "FIPS compliance" switch that is set to ON or OFF. When set to ON, FIPS will apply to the SFTP and FTP/S services created at the domain level (FIPS is not supported for global services). The FIPS compliance switch does not apply to the HTTP/S service, because FIPS is switched on in a different location for the HTTP/S protocol (the links in the note below discuss configuring FIPS for all supported protocols, including HTTP/S).