Amazon S3 network storage
The Amazon S3 network storage option allows you to use existing Amazon S3 Cloud object storage as additional storage space.
Adding the Amazon S3 network storage
In the desired domain, navigate to the ACCOUNTS > Network Storage module. Click on the Add button, or right click anywhere in the grid area and select Add from the pop-up menu. In the Add Network Storage dialog window, select Amazon S3 as the Protocol, then click OK. The Add "Amazon S3" Network Storage dialog will appear as depicted in the image below.
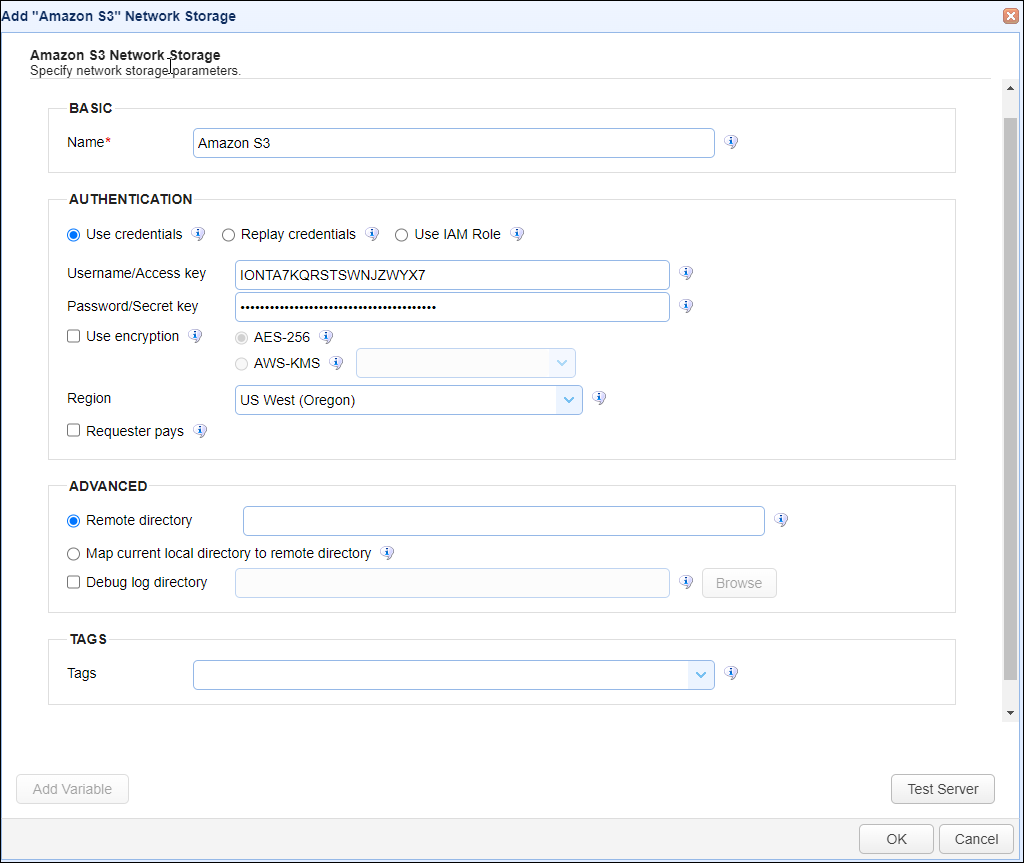
Basic
Name - The unique name for this network storage.
Authentication
Use Credentials - If selected, enter the Username/Access key and Password/Secret Key fields, which will be used to authenticate access to the Amazon S3 Storage.
-
Username/Access key - The Username/Access key
-
Password/Secret key - The Password/Secret key
Replay credentials - If selected, uses the current user's credentials to authenticate the Amazon S3 Storage instead of a static Username/Access key and Password/Secret key. Note: This feature will not work for users who authenticate to the MFT Server using the SFTP service via public key authentication.
Use IAM Role - If selected, uses the Identity and Access Management role for authentication.
When connecting to an Amazon S3 trading partner and/or network storage using the IAM Role, it assumes the role provided by the EC2 metadata. While this works for most instances, it does not work when using a Kubernetes cluster. Therefore, below you will find instructions on how to access an AWS S3 Bucket from a K8 Cluster using the IAM role feature.
Create an IAM role with the following policy document. Replace jscape-test-eks-bucket with your bucket name.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:PutObject",
"s3:ListBucket",
"s3:DeleteObject",
"s3:PutObjectAcl"
],
"Resource": [
"arn:aws:s3:::jscape-test-eks-bucket",
"arn:aws:s3:::jscape-test-eks-bucket/*"
]
}
]
}
Attach the IAM role to the cluster's node or instance.
Create a JSCAPE MFT pod using the Docker Instructions below:
Note: Modify the Policy document if the MFT needs to access more S3 buckets.
Use encryption - If checked, enables encryption for the network storage. Choose either AES-256 or AWS-KMS server-side encryption. AES-256 uses Amazon S3 managed keys, and AWS-KMS uses AWS KMS managed keys. AWS-KMS keys are created in AWS via the Key Management Service. The dropdown for this field pulls in a list of available keys from AWS.
Region - Select the Amazon region where the S3 bucket resides.
Requester pays - If checked, configure an Amazon S3 bucket to be a requester pays bucket, meaning the requester pays the cost of the request and data download instead of the bucket owner.
Advanced
Remote directory - If selected, maps the local virtual path to a specific remote path on the target server.
Map current local directory to remote directory - If selected, maps the local virtual path to remote path having the same name as the local virtual path. For example, if network storage is mapped to virtual path /path, then when connecting to the network storage, it will drop the user in /path directory on target server.
Debug log directory - If checked, this is the directory in which to store debug logs for this network storage.
Tags
Tags - If specified, this is the one or more tags that are used to limit which administrators have access to the network storage.