Microsoft Azure Blob Service network storage
This Network Storage type uses Microsoft Azure Blob storage as additional storage space.
Adding the Microsoft Azure Blob Service Network Storage
In the desired domain, navigate to the ACCOUNTS > Network Storage module. Click Add. The Add Network Storage window displays. Select Microsoft Azure Blob Service as the Protocol, then click OK. The Add "Microsoft Azure Blob Service" Network Storage dialog appears as shown in the image below.
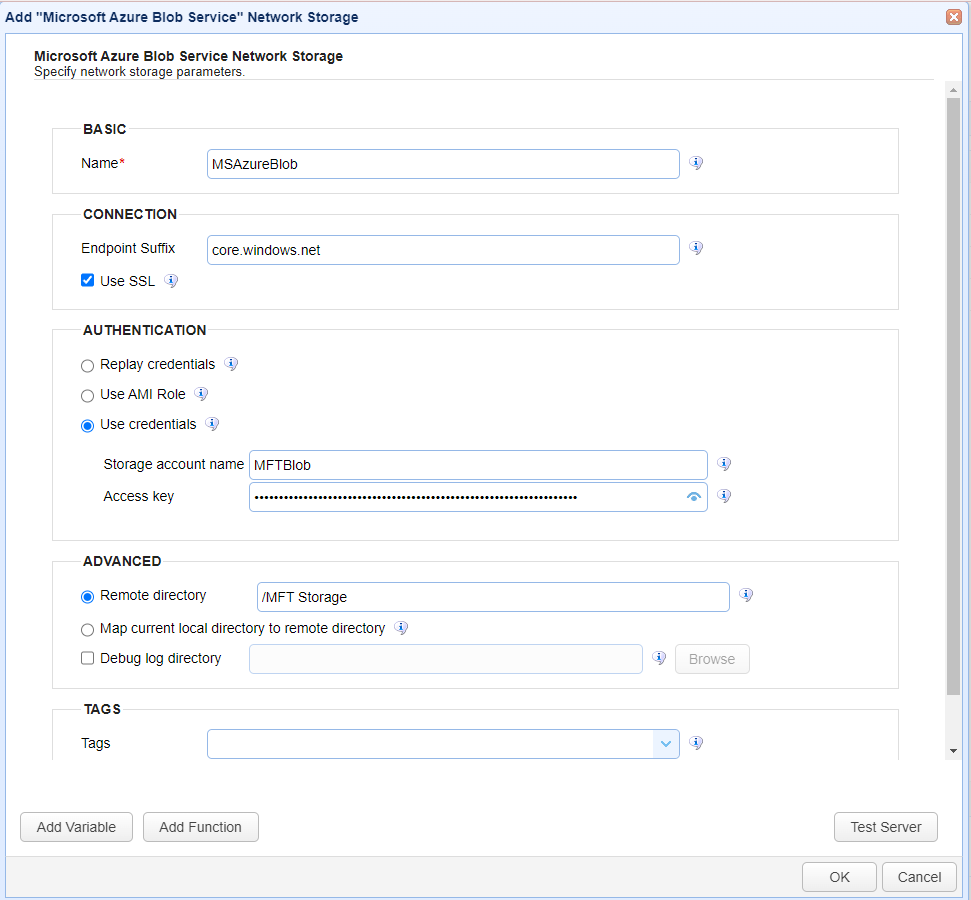
Below is a description of the Azure Blob Network Storage fields.
BASIC
Name — Identifies the unique name for this network storage.
Connection
Endpoint Suffix — Identifies the endpoint suffix for the Azure Blob Service Network Storage. The default value is core.windows.net.
Use SSL — If selected, SSL protection is enabled for this Network Storage.
AUTHENTICATION
Replay credentials — If selected, the current user's credentials are used instead of static credentials.
ACCOUNTS > Users > Users > Add/Edit > Require public key authentication for SFTP.
Use AMI Role — If selected, a system-assigned or user-assigned Azure Managed Identity is used for authentication.
System-assigned Managed Identify
On the Azure resource (e.g., the VM) where MFT Server is installed, navigate to the Identity section and enable System-assigned managed identity.
Using the Azure portal, navigate to your Blob Storage account.
Under Access Control (IAM), click Add Role Assignment.
Select a role that provides the necessary access, such as Storage Blob Data Contributor (for read, write and delete access to blobs).
In the Select box, search for and choose your VM’s system-assigned Managed Identity. Click Save to apply the role assignment.
User-assigned Managed Identity
Using the Azure portal, create a Managed Identity.
On the Azure resource (e.g., VM) where MFT Server is installed, assign the Managed Identity under the Identity > User Assigned tab.
Using the Azure portal, navigate to your Blob Storage account.
Under Access Control (IAM), click on Add Role Assignment.
Select a role that provides the necessary access, such as Storage Blob Data Contributor (for read, write, and delete access to blobs).
In the Select box, choose your VM’s user-assigned managed identity. Click Save to apply the role assignment.
Use credentials — If selected, enables the administrator to specify a static storage account name and access key.
Storage account name — Identifies the storage account name for the remote Microsoft Azure Blob Service. This is the unique namespace for your data.
Access key — Identifies the access key for the Azure Blob Service Network Storage. Not applicable if using the AMI Role or Reply credentials authentication methods.
Advanced
Remote directory — If selected, maps the local virtual path to a specific remote path on the target (Blob Storage Container) server.
Map current local directory to remote directory — If selected, maps the local virtual path name to the remote path name. For example, if Network Storage is mapped to virtual path "/mypath", the user is placed in the "/mypath" directory when connecting to the target server.
Debug log directory — If selected, identifies the directory where debug logs are stored for the Network Storage.
TAGS
Tags — If specified, identifies one or more tags used to limit administrator access to the Network Storage.