Okta example using SAML
Okta is an identity management service. It gives users access to various software with one successful Okta log in. This example provides step-by-step instructions on how to set up MFT Server using the Okta admin console and the MFT Server Manager. When complete, an MFT Server Administrator will be able to log in to the MFT Server Manager using Okta. The images provided under the Okta Instructions are taken from the Okta Admin console. Most images are snippets and not the complete page.
Okta Instructions
-
Sign in to the Okta admin console.
-
Using the left sidebar menu, navigate to Applications > Applications.
-
Click on the Create App Integration button.
-
In the Create a new app integration pop-up dialog, choose SAML 2.0 and click Next.
In the CreateSAML Integration dialog:
-
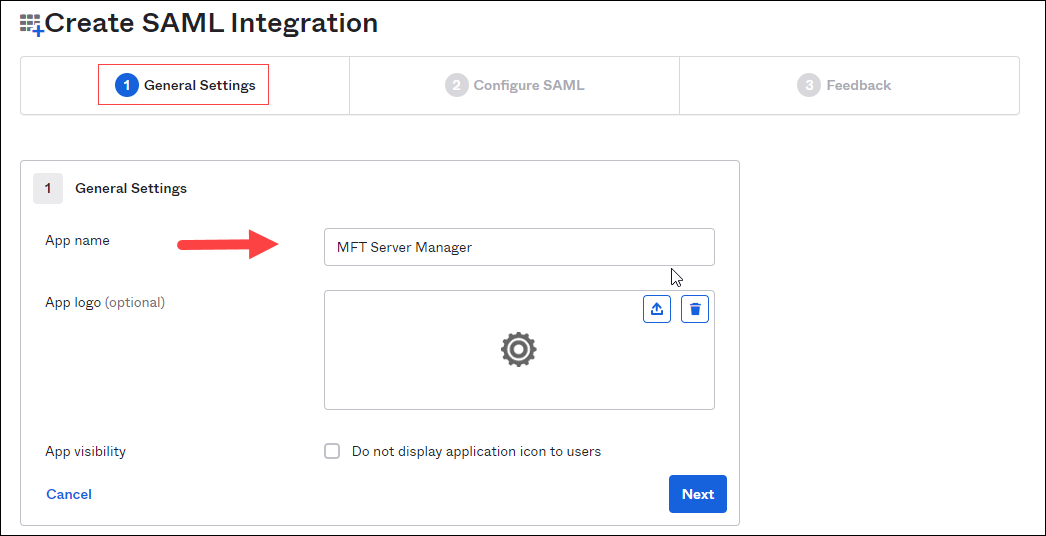
(1) General Settings - enter an App name (for example: MFT Server Manager). See the image below. Click Next.
-
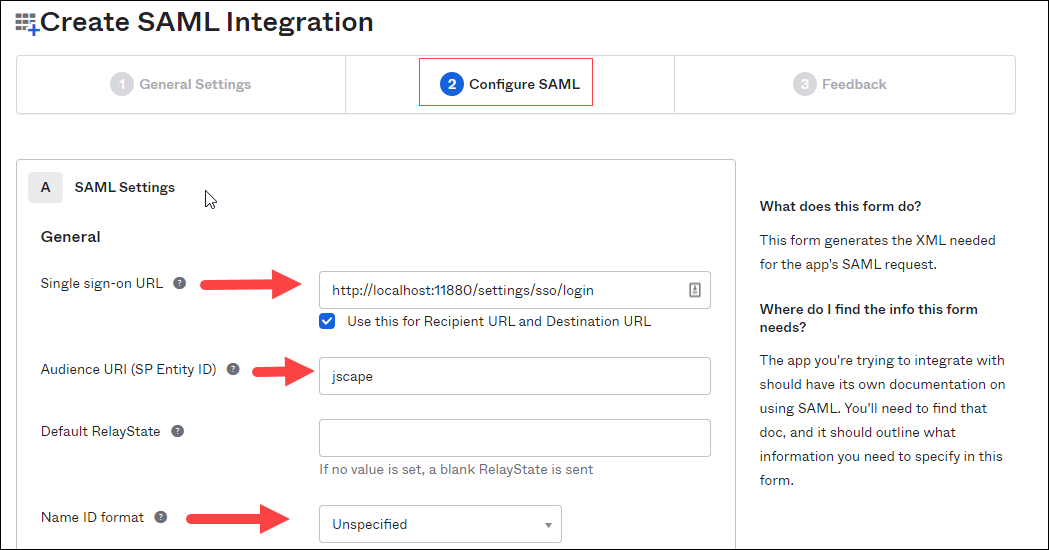
(2) Configure SAML, enter values for the following: (See the image below).
-
Single sign-on URL - use the URL format: http://[hostname:administrative_port]/settings/sso/login (for example: http://localhost:11880/settings/sso/login).
-
Audience URI (SP Entity ID) - any ID (for example: jscape).
-
Name ID format - This value should remain Unspecified. Click Next.
-
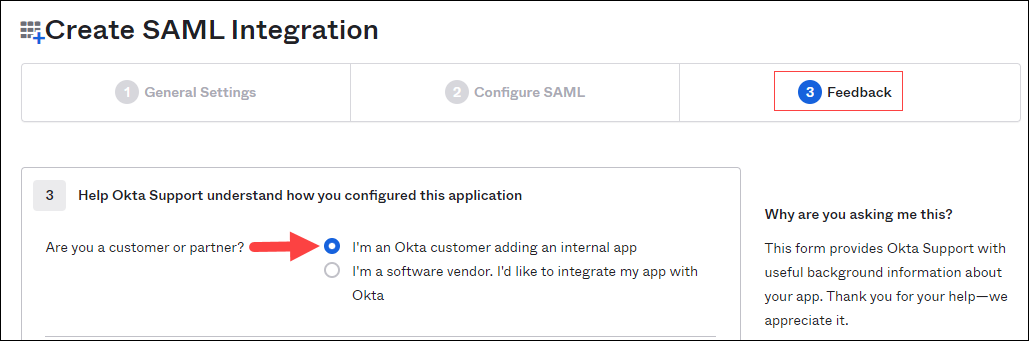
(3) Feedback: select I'm an Okta customer adding an internal app, then click Finish. See the image below.
The page will refresh displaying the App name you entered previously, and the Sign On tab will be active. See the image below.
-
On this page, scroll down to the SAML Signing Certificates section. then click on View SAML setup instructions.
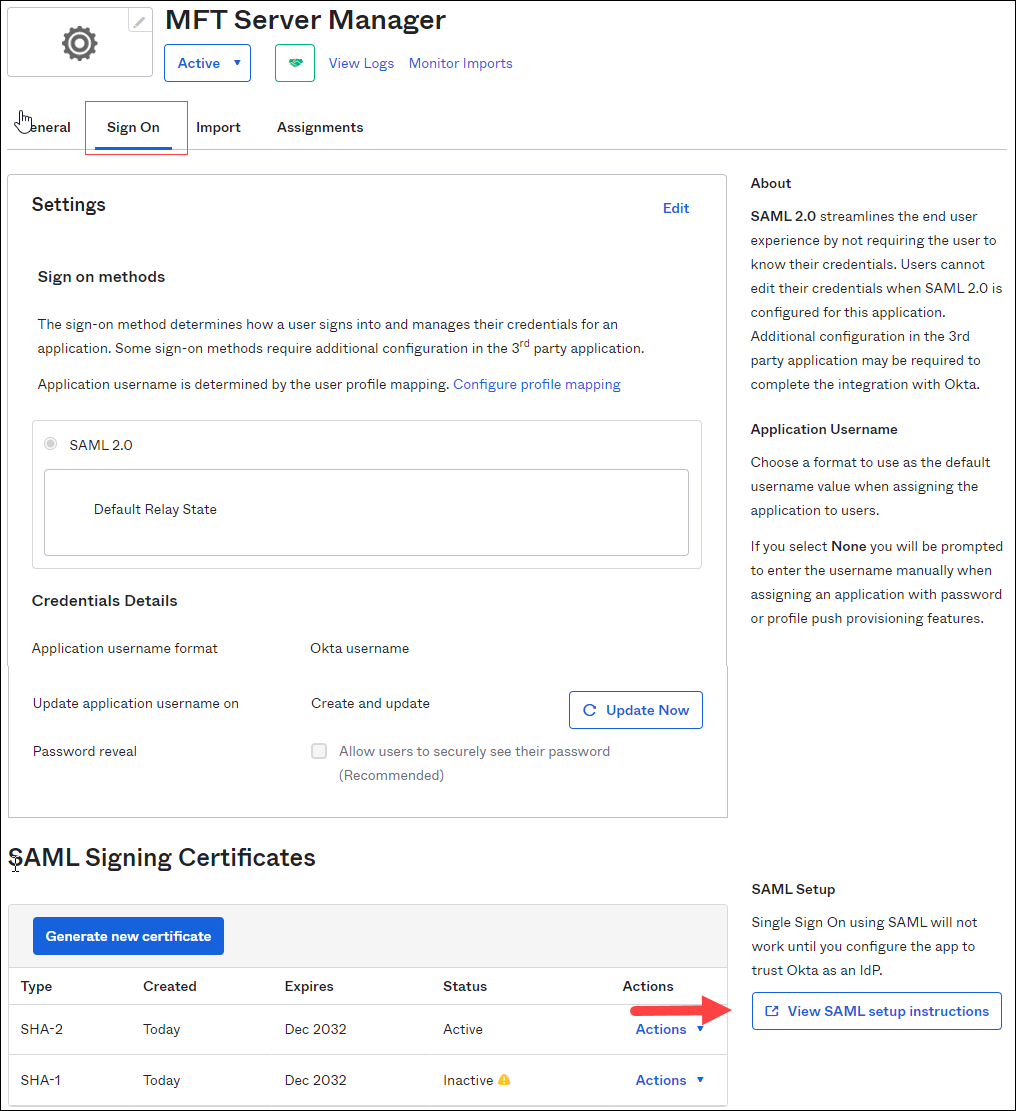
-
A new page will open with Idp details. Copy the Identity Provider Single Sign-On URL value and download the X.509 Certificate. You will need the URL and certificate when configuring this feature in the MFT Server Manager.
-
Using the left menu, navigate back to Applications > Applications.
-
Click the Assign Users to App button. Check the following:
-
Under the Application & Label list, check the application you specified in Step 5.
-
Under the Person & Username, check the User who will be accessing the . See the image below. Click Next.
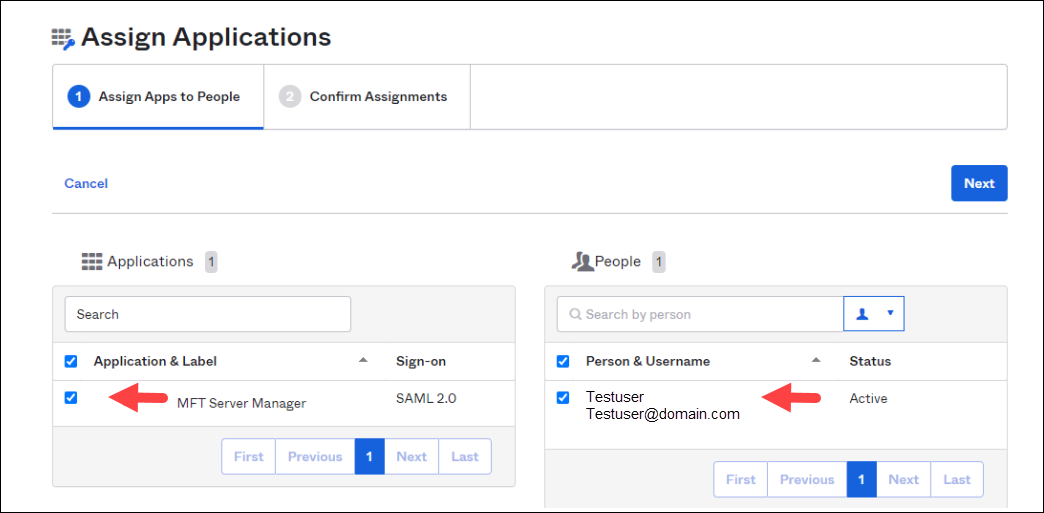
-
Click on Confirm Assignments button.
This completes the Okta configuration.
MFT Server Instructions
Launch the MFT Server Manager.
Click on Keys > Host Keys. Click on Import, then select Import File from the dropdown list. The Import Public Key dialog will appear.
Key alias - enter the desired alias name.
Key file - enter the file name you downloaded in Step 9 of the Okta instructions.
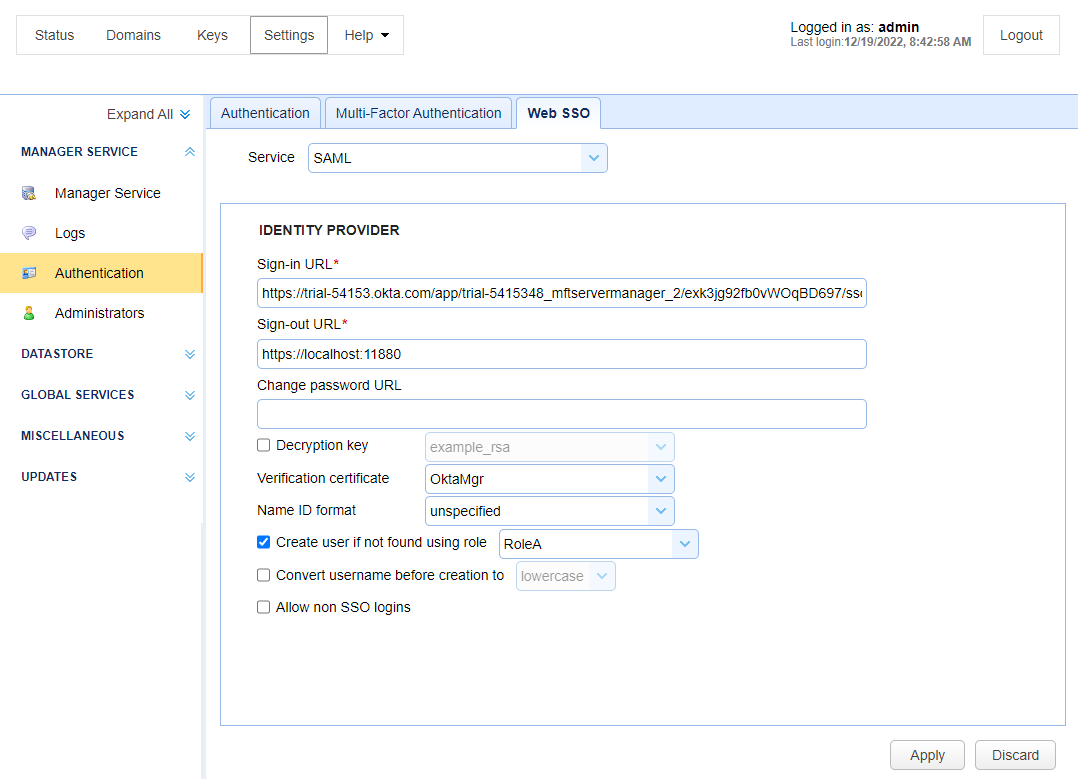
Click on Settings > MANAGER SERVICE > Authentication > Web SSO tab.
Service - select SAML from the dropdown list.
Sign-in URL - paste the URL you copied in Step 9 of the Okta instructions.
Sign-out URL - enter the desired sign-out URL (for example:. http://localhost:11880).
Verification Certificate - select the Host Key that you imported into Keys > Host Keys.
Create user if not found using role - check this box to allow the system to create the Admin user if they don't already exist in the Settings > MANAGER SERVICE > Administrators > Administrators grid.
Log in to the MFT Server Manager using a URL with this format: http://<host>:<port>/settings/sso/login (for example: http://localhost:11880/settings/sso/login).
If you have already authenticated with the Okta identity provider, you will be automatically logged in to the MFT Server Manager.
If you have not authenticated with the Okta identity provider, you will be presented with the Okta log in page. If you successfully authenticate, the MFT Server Manager will load.
Note: New Admin user - If the user logging in is a new Admin user, not yet in the Settings > MANAGER SERVICE > Administrators > Administrators grid, the same behavior will occur as described above only if the Create user if not found using role field is checked, as depicted in the image below. When checked, the Admin user is automatically added to the Administrator table after the first-time they successfully authenticate. If the Create user if not found using role field is not checked, the user will be presented with the standard MFT Server Manager log in page and they will not be able to log in using Okta SSO. If Allow non SSO logins is not checked (as depicted in the image below), then only Okta SSO log in's will be allowed.