FIPS 140-2
Federal Information Processing Standards (FIPS) is a U.S. government computer security standard that specifies the security requirements for cryptographic modules used to protect sensitive information.
FIPS can be enabled for:
-
HTTP/S service (enabled system wide)
-
MFT Server Management REST API
-
FTP/S and SFTP/SCP services (enabled at the domain level)
MFT Server supports FIPS 140-2 and 140-3. This includes SaaS and on-premises installations. See FIPS 140-3 to enable this version.
To configure FIPS 140-2 on-premises, see the instructions below. To configure FTPS 140-2 in a SaaS environment, contact Technical Support.
Configuring MFT Server for FIPS 140-2
High-level overview. Enabling FIPS requires:
-
Setting the appropriate MFT Server fields associated with the FIPS feature
-
Copying files from one MFT Server directory to another
-
Restarting the MFT Server service
1) Setting MFT Server fields to enable FIPS
Enabling FIPS for HTTP/S
Enabling FIPS for HTTP/S is a system-wide action. Follow the steps below.
Navigate to
Settings > MISCELLANEOUS > Web > Web
Select
Enable FIPS compliance.
Click the
SSL/TLS Ciphersbutton. The SSL/TLS Cipher Suites dialog displays.
Click this link for supported ciphers.
When operating in FIPS mode, it is crucial to select only supported ciphers. The system does not perform a validation check to confirm the ciphers you have chosen are compliant or supported while FIPS is active.
Enabling FIPS for the MFT Server (Management) REST API
Follow the steps below to enable FIPS when accessing the REST API. .
Navigate to
Settings > MISCELLANEOUS > Web > REST
Select
Enable FIPS compliance.
Click the
SSL/TLS Ciphersbutton. The SSL/TLS Cipher Suites dialog displays.
Click this link for supported ciphers.
Enabling FIPS for FTP/S and SFTP/SCP on the Domain level
Navigate to [Domain] >
SECURITY > Compliance > FIPS.
Set
FIPS complianceto ON.
Select ciphers for FTP/S (if you are enabling FIPS for this protocol)
Navigate to [Domain] >
SERVICES > Listeners > FTP/S. Click onSSL/TLS Ciphers...The SSL/TLS Cipher Suites dialog displays.
See this link for supported ciphers.
Select algorithms for SFTP/SCP (if you are enabling FIPS for this protocol)
Navigate to [Domain] >
SERVICES > Listeners > SFTP/SCP. Click onAlgorithms...The SFTP/SCP Algorithms dialog displays.
See this link for supported algorithms.
When operating in FIPS mode, It is crucial to select only supported algorithms and ciphers. The system does not perform a validation check to confirm the algorithms you have chosen are compliant or supported while FIPS is active.
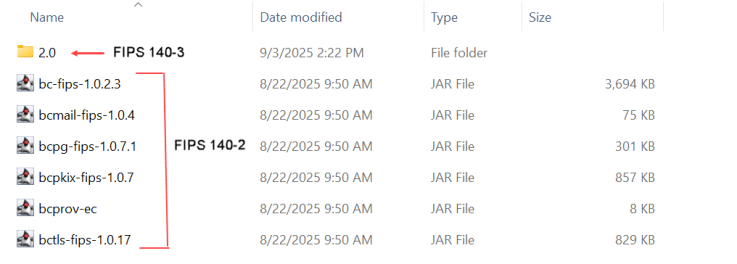
2) Copy Files from fips directory to libs directory
-
Go to the <MFT Server installation>/libs directory. Copy or move all the jar files that start with bc (Bouncy Castle libraries - bc*) to a backup directory of your choosing. This is in case they are needed in the future.
-
Go to the <MFT Server installation>/fips directory. Copy all the jar files in this directory to the <MFT Server installation>/libs directory.
3) Restart the MFT Server service.