Web SSO authentication
Single-Sign-On (SSO) lets Users log in to one service (identity provider), which then automatically grants access to other services (service provider) without requiring a separate login.
MFT Server supports web-based SSO using SAML, OpenID, and OpenID Connect-compliant identity providers. Consult your identity provider's documentation for information on how to enable and configure SSO.
Login URL
To perform a web SSO log in, use the following URL format:
https://[hostname]/sso/[domainname]/login
https://1.2.3.4/sso/mydomain/login
You are automatically logged in to MFT Server if you previously authenticated with your identity provider. If you did not previously authenticate, you are redirected to your identity provider's sign-in URL. After authenticating with your identity provider, you are automatically logged in to MFT Server.
Note:
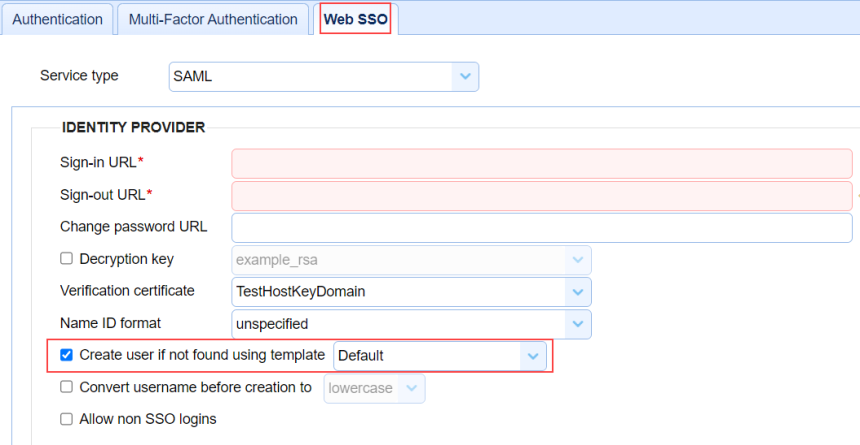
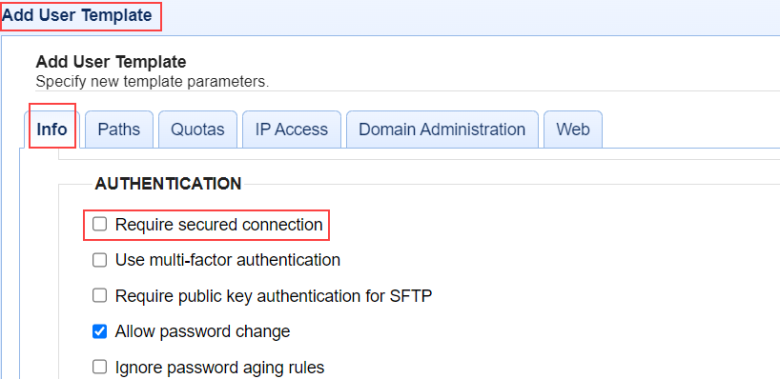
When configuring Web SSO for any Service type, you have the option to let MFT Server create a User account (if it does not exist) for the new User logging in. The field that controls this behavior is Create user if not found using template <Template Name>. If this field is selected, you must decides if you will allow a secure or non-secure connection, which is controlled by a field in the Template specified. The field name is Require secured connection. When selected (for new templates, it is checked by default), only connections using HTTPS are allowed. See the images below.
[Domain] > ACCOUNTS > Authentication > Web SSO
[Domain] > ACCOUNTS > Users > Templates
See also
Redwood University - Authentication Preferences.Select Web SSO.